A Best Practice Guide
|
|
|
- Vivian Newton
- 10 years ago
- Views:
Transcription
1 A Best Practice Guide Contents Introduction [2] The Benefits of Implementing a Privacy Management Programme [3] Developing a Comprehensive Privacy Management Programme [3] Part A Baseline Fundamentals of a Privacy Management Programme [3] Part B Ongoing Assessment and Revision [9] Privacy Management Programme At a Glance [11]
2 A Best Practice Guide Introduction Privacy Management Programme per se is not a requirement under the Personal Data (Privacy) Ordinance ( the Ordinance ). However, the Privacy Commissioner for Personal Data ( the Commissioner ) advocates that organisational data users should embrace personal data privacy protection as part of their corporate governance responsibilities and apply them as a business imperative throughout the organisation, covering business practices, operational processes, product and service design, physical architectures and networked infrastructure. To this end, a privacy management programme serves as a strategic framework to assist an organisation in building a robust privacy infrastructure supported by an effective on-going review and monitoring process to facilitate compliance with the requirements under the Ordinance. It also demonstrates the organisation s commitment to good corporate governance and building trust with its employees and customers through open and transparent information policies and practices. Constructing a privacy management programme within an organisation takes careful planning and consideration across disciplines and job functions. Employees should be aware of and understand the applicable parts of the organisation s privacy management programme. Customers and business partners should likewise be made aware of and given assurance, where appropriate, in the relevant aspects of the privacy management programme. Privacyrelated obligations and risks should be correctly identified and appropriately taken into account in developing business models and related technologies and business practices before new products or services are launched. Risks of data breaches should be minimised and the effects of any data breaches mitigated. There will be times when mistakes are made. However, with a solid privacy management programme, organisations will be able to identify their weaknesses, strengthen their good practices, demonstrate due diligence, and potentially raise the protection of personal data that they hold to a higher level than the bare minimum needed to meet legal requirements. This Best Practice Guide ( this Guide ) outlines what the Commissioner advocates as good approaches for developing a sound privacy management programme, but it is not a one-size-fits-all solution. Each organisation will need to determine, taking into consideration its size and nature of business, how best to apply this Guide to develop its own privacy management programme. For the avoidance of doubt, this Guide does not constitute a Code of Practice under section 12 of the Ordinance or a Guidance Note which, in the traditional regulatory sense, provides direct guidance for compliance with specific provisions of the Ordinance. No specific legal liability will be incurred directly if an organisation elects not to observe the advice and recommendations contained in this Guide. The word should used in the context of this Guide represents the Commissioner s advocacy of the best practice instead of imposing prescriptive obligations to be met by organisations. Part A of this Guide outlines the baseline fundamentals or components of a privacy management programme. Elements such as organisational commitment and programme controls are important. Privacy Management Programme: A Best Practice Guide 2 February 2014
3 Part B discusses how to maintain and improve a privacy management programme on an ongoing basis. A privacy management programme should never be considered a finished product; it requires ongoing assessment and revision in order to be effective and relevant. The components should be regularly monitored, assessed and updated accordingly to keep pace with changes both within and outside the organisation. This may encompass changes in such areas as technology, business models, law and best practices. The Benefits of Implementing a Privacy Management Programme Every organisation that is subject to the Ordinance is obliged to comply with the statutory requirements therein. A comprehensive privacy management programme provides an effective way for organisations to assure themselves of compliance. But it is more than that. It helps foster a privacy respectful culture throughout an organisation. This is conducive to building trustful relationships with customers, employees, shareholders and regulators. When an organisation walks the talk by implementing a robust privacy management programme, enhanced trust from stakeholders including customers to engage with that organisation should follow. An organisation that has a strong privacy management programme may enjoy an enhanced reputation that gives it a competitive edge. Conversely, without strong personal data protection, trust may erode to an organisation s detriment. Personal data breaches can be expensive for organisations both in terms of clean up and reputation repair. Breaches may also prove expensive for the affected individuals. Given the vast amounts of personal data held by organisations and institutions, the increasing economic value of the data, and the heightened attention and concern regarding privacy breaches, it makes business sense for organisations to take steps to put in place and maintain privacy management programmes to minimise the risks of such breaches, maximise the organisation s ability to address the underlying problems, and minimise the damage arising from breaches. Developing a Comprehensive Privacy Management Programme Part A Baseline Fundamentals of a Privacy Management Programme What should an organisation do to ensure that it is handling personal data appropriately? How will it know that it is doing it right? How will it be able to demonstrate to itself, its customers, the public and the Commissioner that it has the capacity to comply and has complied with the Ordinance? Organisations are advised to appoint someone to oversee the development, implementation and maintenance of the organisation s personal data protection programmes and practices. Policies and processes are needed, and training of employees is required. Contracts (or other means) are required when organisations transfer personal data to data processors for processing, to ensure that the data is protected in a manner that is comparable to how the organisation would protect it. Organisations should have systems in place to respond to data access and correction requests from individuals for their personal data, and to respond to complaints from employees and customers about infringement of personal data privacy. Privacy Management Programme: A Best Practice Guide 3 February 2014
4 This part outlines the key components of a privacy management programme. 1 (a) Organisational Commitment This first component is an internal governance structure that fosters a privacy respectful culture. Organisations should develop and implement programme controls that give effect to the data protection principles in Schedule 1 to the Ordinance. Compliance with the legal requirements in an effective and responsible manner, however, requires organisations to have a governance structure, or at the minimum, processes to follow and the means to ensure that they are being followed. A privacy respectful culture needs to be cultivated. Buy-in from the Top Top management support is key to a successful privacy management programme and essential for a privacy respectful culture. When top management is committed to ensuring that the organisation is accountable, the programme will have a better chance of success, and a privacy respectful culture will more likely be established. Top management needs to support the privacy management programme. Depending on the organisation structure, top management or its delegated authority should: appoint the Data Protection Officer(s); endorse the programme controls; and report to the Board, as appropriate, on the programme. (b) Data Protection Officer/Data Protection Office Organisations should appoint or designate someone to manage the privacy management programme. Whether this person is a senior executive of a major corporation or the owner/operator of a very small organisation, someone should be assigned responsibility for overseeing the organisation s compliance with the Ordinance (herein referred to as the Data Protection Officer ). The Data Protection Officer may or may not be a full-time job. In larger organisations, the Data Protection Officer may need to be supported by dedicated staff. Also, while other individuals may be involved in handling personal data, the Data Protection Officer is usually the one responsible for structuring, designing and managing the programme, including all procedures, training, monitoring/ auditing, documenting, evaluating, and follow-up. Resources should be channeled to train and develop the Data Protection Officer and/or his team as a professional in personal data privacy protection. The Data Protection Officer can play many roles with respect to personal data protection. Typically, the Data Protection Officer will: establish and implement programme controls; coordinate with other appropriate persons responsible for related disciplines and functions within the organisation; be responsible for the ongoing assessment and revision of programme controls; represent the organisation in the event of an enquiry, an inspection or an investigation by the Commissioner; and advocate personal data protection within the organisation itself. Privacy Management Programme: A Best Practice Guide 4 February 2014
5 (c) The last role is as important as the others. Organisations face competing interests and personal data protection is one programme of many. Personal data protection should be seen not just as legal compliance but also in terms of improving processes, customer relationship management, and reputation. The privacy management programme s importance should be recognised at all levels. It is important to build this into every major function involving the use of personal data, including product development, customer services or marketing initiatives. Reporting Reporting mechanisms should be established, and reflected in the organisation s programme controls. The organisation should establish internal reporting mechanisms to ensure that the right people know how the privacy management programme is structured and whether it is functioning as expected. Within larger organisations, the audience for this information is likely to be top management, and in turn, top management reports to the board of directors. All reporting mechanisms should be reflected in the organisation s programme controls. Organisations should establish some form of internal audit and assurance programmes to monitor compliance with their personal data protection policies. This could include the form of customer and employee feedback for smaller organisations, or for some larger organisations, third-party verifications. Should the organisation be subject to an enquiry, an inspection or an investigation under the Ordinance, these reports may be helpful in demonstrating the organisation s compliance with the Ordinance. 2 However, there is more to reporting than this. There will be times when escalation of personal data issues should be considered, for example, when there is a security breach or in case of complaints. Escalation means both involving people of relevant responsibility and ensuring that the needed persons in the organisation are included in the resolution of the issue. In large organisations, this could include, for example, representatives from technical, legal and corporate communications streams. How and when to escalate should be clearly defined and explained to employees. To ensure that related processes are being followed, organisations may need to monitor whether the necessary steps are being taken when triggered. Some organisations have found it useful to conduct test runs, for example, for their personal data breach identification, escalation and containment protocols. An effective reporting programme: clearly defines its reporting structure (in terms of reporting on its overall compliance activities) as well as employee reporting structures in the event of a complaint or a potential breach; tests and reports on the results of its internal reporting structures; and documents all of its reporting structures. Programme Controls Programme controls form the second component of a privacy management programme. These help ensure that what is mandated in the governance structure is implemented in the organisation. This section identifies the programme controls in a privacy management programme. Developing these controls will assist the Data Protection Officer in structuring Privacy Management Programme: A Best Practice Guide 5 February 2014
6 (a) an appropriate privacy management programme within the organisation and the controls will be used to demonstrate how the organisation is compliant with the Ordinance. Personal Data Inventory Whether it has a sophisticated privacy management programme in place or is implementing a new one, every organisation can benefit from carefully examining the personal data it holds and how it currently handles the data. An organisation should know what kinds of personal data it holds (for example, personal data of employees, personal data of customers, etc.), how the personal data is being used and whether the organisation really needs it at all. Understanding and documenting the types of personal data that an organisation collects and where it is held (e.g. whether or not the data has been passed to any data processor) are important. This will affect the type of consent the organisation obtains from individuals and how the data is protected; and it will make it easier to assist individuals in exercising their data access and correction rights. Every component of an accountable, effective privacy management programme begins with this assessment. Every organisation should be clear about: what kinds of personal data it holds and where it is held (i.e. within the organisation or by the data processor(s)) and document this assessment; and why it is collecting, using or disclosing personal data and document these reasons. (b) Policies Organisations should develop and document internal policies that address obligations under the Ordinance. These policies should be made available to employees who should be reminded of these policies and any updates periodically. Organisations will wish to develop internal policies that give effect to the six data protection principles in the Ordinance. These policies should be documented and should show how they connect to the legal requirements. The key policies that organisations should have in place are the following: Collection of personal data; Accuracy and retention of personal data; Use of personal data including the requirements for consent; Security of personal data; Transparency of organisations personal data policies and practices; and Access to and correction of personal data. Organisations should also incorporate personal data compliance requirements in other policies of the organisation, as appropriate. For example, in contract management policies, procurement policies, human resources policies and policies dealing with the disclosure of personal data to regulatory bodies, law enforcement agencies and other government bodies. Organisations are advised to refer to the guidance notes issued by the Commissioner on various subjects of data protection. Privacy Management Programme: A Best Practice Guide 6 February 2014
7 (c) Risk Assessment Tools Personal data risks evolve over time. Conducting periodic risk assessments, in particular when there is material change to the regulatory requirements relating to personal data or before making any material change to the data user s existing personal data process or introducing a new personal data process, is an important part of any privacy management programme to ensure that the policies and practices of organisations are and remain compliant with the Ordinance. Sometimes organisations offer services which collect, use or disclose personal data but which have not been thoroughly vetted from a privacy perspective. Proper use of risk assessment tools can help prevent problems. Fixing a personal data problem after the fact can be costly so careful consideration of the purposes for a particular initiative, product or service, and an assessment that minimises any personal data impacts beforehand is vital. As a result, such assessments should be conducted throughout the organisation for all new projects involving personal data and on any new collection, use or disclosure of personal data in ways that are materially different from existing practice. Organisations should develop a process for identifying and mitigating leakage and security risks, which could include the use of privacy impact assessments. The Data Protection Officer should play an advisory or consultative role. The Information Leaflet Privacy Impact Assessments 1 issued by this Office provides assistance in this regard. (d) Training and Education Requirements A sound privacy management programme requires all relevant members (i.e. those handling personal data) of an organisation to be aware of, and be ready to act on personal data protection obligations. Up-to-date training and education requirements for all relevant employees, tailored to specific needs, are key to an effective privacy management programme. In order for a privacy management programme to be effective, relevant employees should be made aware of personal data protection generally and to be conversant with the organisations policies and practices for compliance with the requirements under the Ordinance. Those who handle personal data directly may need additional training specifically tailored to their roles. Training and education need to be current and relevant. To facilitate this, attending this Office s professional workshops and arranging in-house train-the-trainer programmes would be helpful. Employees will be able to better protect personal data when they are able to recognise a matter as one that involves personal data protection. Organisations may have very sound policies and programme controls in place but if employees do not follow them, the privacy management programme has broken down. Relevant employees should be reminded to comply with the organisation s policies and programme controls as an integral part of their duties. There are many ways for organisations to deliver training and general personal data protection education. Examples include providing mandatory training modules on the company intranet, small group sessions, one-on-one training, monthly e-newsletters, or inserting modules within training on organisation policies. The organisation should document its training processes and measure participation and success. 1 Privacy Management Programme: A Best Practice Guide 7 February 2014
8 (e) For personal data protection training and education to be effective, it should: be given to new employees in its induction programme and periodically thereafter; cover the policies and procedures established by the organisation; be delivered in an appropriate and effective manner, based on organisational needs; and circulate essential information to relevant employees as soon as practical if an urgent need arises. Breach Handling Personal data breaches are expensive on many fronts and taxing on consumer trust. Organisations should have a procedure in place and an officer or a designated team responsible for managing a personal data breach. Responsibilities for internal and external reporting of the breach should be clear. While reporting of major data breach to the Commissioner is not mandatory under the Ordinance, the Commissioner encourages organisations to adopt a procedure of notification in handling a data breach. In handling personal data breach, organisations should consider the circumstances of the breach, and decide whether any of the following persons should be notified as soon as practicable: the affected data subjects; the law enforcement agencies; the Commissioner; any relevant regulators; and (f) such other parties who may be able to take remedial actions to protect the personal data privacy and the interest of the data subjects affected (for example, Internet search companies may assist to remove relevant cached link from its search engine). Guidance on Data Breach Handling and the Giving of Data Breach Notifications 2 issued by this Office provides practical guidance in this regard. Data Processor Management Personal data handling by data processor is another key area to consider. Are there contractual or any other means in place to protect the personal data? The types of obligations to be imposed on data processor should include the following: security measures to be taken by the data processor; timely return, destruction or deletion of the personal data no longer required; prohibition against other use and disclosure; prohibition (absolute or qualified) against sub-contracting to other service provider; reporting of irregularity; measures to ensure contract staff s compliance with the agreed obligations; organisation s right to audit and inspect; and consequences for violation of the contract. Organisations are advised to take note of the Information Leaflet Outsourcing the Processing of Personal Data to Data Processors 3 issued by this Office Privacy Management Programme: A Best Practice Guide 8 February 2014
9 (g) Communication Organisations should take all practical steps to ensure employees and customers can ascertain their personal data policies and practices. This communication should be clear and easily understandable and not simply a reiteration of the Ordinance. In general, it should: provide enough information so that the public knows the purpose of the collection, use and disclosure of personal data and how long it is retained; include information on who to contact with questions or concerns; and be made easily available to individuals. 2 The Data Protection Officer or Data Protection Office should develop an oversight and review plan on a periodic basis that sets out how and when the effectiveness of the privacy management programme will be monitored and assessed, as outlined in organisational commitments. Depending on the organisation s compliance and control infrastructure, such plan may be covered in its overall oversight and review system. The plan should establish performance measures and include a schedule of when the policies and other programme controls will be reviewed. Assess and Revise Programme Controls The effectiveness of programme controls should be monitored, periodically audited, and where necessary, revised. Individuals should be made aware of their ability to access their personal data held by the organisation, and how to request correction or to enquire about the organisations compliance with the Ordinance. Part B Ongoing Assessment and Revision Part A describes the components for creating a privacy management programme. Part B of this Guide outlines the basic tasks involved in the maintenance of a privacy management programme to ensure ongoing effectiveness, compliance and accountability. In order to properly protect personal data and meet legal obligations, organisations should monitor, assess and revise their framework to ensure it remains relevant and effective. 1 Develop an Oversight and Review Plan An oversight and review plan will help the organisation keep its privacy management programme on track and up to date. Monitoring is an ongoing process and should at least address the following questions: what are the latest threats and risks? are the programme controls addressing new threats and reflecting the latest complaint or audit findings, or guidance of the Commissioner? are new services being offered that involve increased collection, use or disclosure of personal data? is training necessary and if yes, is it taking place, is it effective, are policies and procedures being followed, and is the programme up to date? If problems are found during the monitoring process, concerns will need to be documented and addressed by the appropriate officers. Critical issues should be brought to the attention of top management. Privacy Management Programme: A Best Practice Guide 9 February 2014
10 For critical or high-risk processes, periodic internal or external audits are important ways to assess the effectiveness of an organisation s privacy management programme. Otherwise, it is recommended that the Data Protection Office should conduct periodic assessments to ensure key processes are being respected. For smaller organisations or for less formal reviews, organisations should develop checklists that are reviewed on a regular basis. Through whatever means appropriate, organisations need to put in place practical measures to ensure that employees or contractors are following the organisation s policies and programme controls. As stated, this document is not a onesize-fits-all solution. Each organisation will need to decide how to structure its own privacy management programme, taking into consideration a number of factors, including the size of the organisation, the nature of business of the organisation, and the amount and sensitivity of the personal data it handles. Organisation should conduct assessments of its programme controls (as outlined in Part A) in a focused, continuous and thorough manner. Based on the results of the assessment process, the Data Protection Officer should consider whether to take action to update and revise the programme controls. This is a critical responsibility. The changes should be communicated to employees either as they are made or in refresher education and training modules, as appropriate. In short, the following actions should be undertaken by the Data Protection Officer: monitor and update personal data inventory periodically to keep it current and identify and evaluate new collections, uses and disclosures. review and revise policies as needed following assessments or audits, in response to a breach or complaint, new guidance, industrybased best practices, or as a result of environmental scans. treat privacy impact assessments and security threat and risk assessments as evergreen documents so that the privacy and security risks of changes or new initiatives within the organisation are always identified and addressed. review and update training and education on a periodic basis as a result of ongoing assessments and communicate changes made to programme controls. review and adapt breach and incident management response protocols to implement best practices or recommendations and lessons learned from post-incident reviews. review and, where necessary, finetune requirements in contracts with data processors. update and clarify, where necessary, communication explaining personal data policies to the organisation s employees and customers. Privacy Management Programme: A Best Practice Guide 10 February 2014
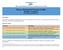
11 Privacy Management Programme At A Glance Part A Baseline Fundamentals Organisational Commitment Buy-in from the Top Data Protection Officer/Office Reporting Top management support is key to a successful privacy management programme and essential for privacyrespectful culture Role exists and is involved where appropriate in the organisation s decisionmaking process Role and responsibilities for monitoring compliance of the Personal Data (Privacy) Ordinance are clearly identified and communicated throughout the organisation Reporting mechanisms need to be established, and they need to be reflected in the organisation s programme controls Responsible for the development and implementation of the programme controls and their ongoing assessment and revision Policy and procedures are in place to incorporate personal data protection into every major function involving the use of personal data Programme Controls The following programme controls are in place: Personal Data Inventory Policies Risk Assessment Tools The organisation is able to identify the personal data in its custody or control The organisation is able to identify the reasons for the collection, use and disclosure of the personal data Covering: Collection of personal data Accuracy and retention of personal data Use of personal data including the requirements of consent Security of personal data Transparency of organisations personal data policies and practices Access to and correction of personal data Training & Education Requirements Breach Handling Data Processor Management Communication Part B Ongoing Assessment and Revision Oversight & Review Plan Develop an oversight and review plan Data Protection Officer or Data Protection Office should develop an oversight and review plan on a periodic basis that sets out how the effectiveness of the organisation s programme controls will be monitored and assessed. Assess & Revise Programme Controls Where Necessary Update personal data inventory Revise policies Treat risk assessment tools as evergreen Update training and education Adapt breach and incident response protocols Fine-tune data processor management Improve communication Privacy Management Programme: A Best Practice Guide 11 February 2014
12 Acknowledgement This Guide is modelled on Getting Accountability Right with a Privacy Management Program (April 2012), available at compiled by the Office of the Privacy Commissioner of Canada, and the Offices of the Information & Privacy Commissioners of Alberta and British Columbia, Canada, by courtesy of the authors. Copyrights Reproduction of all or any parts of this Guide is permitted on condition that it is for non-profit making purposes and an acknowledgement of this work is duly made in reproduction. Disclaimer The information provided in this Guide is for general reference only. It does not provide an exhaustive guide to the application of the Personal Data (Privacy) Ordinance. For a complete and definitive statement of law, direct reference should be made to the Ordinance itself. The Commissioner makes no express or implied warranties of accuracy or fitness for a particular purpose or use with respect to the above information. The above suggestions will not affect the functions and power conferred to the Commissioner under the Ordinance. Office of the Privacy Commissioner for Personal Data, Hong Kong Enquiry Hotline : (852) Fax : (852) Address : 12/F, 248 Queen s Road East, Wanchai, Hong Kong Website : [email protected] Office of the Privacy Commissioner for Personal Data, Hong Kong First published in February 2014
Accountable Privacy Management in BC s Public Sector
 Accountable Privacy Management in BC s Public Sector Contents Accountable Privacy Management In BC s Public Sector 2 INTRODUCTION 3 What is accountability? 4 Steps to setting up the program 4 A. PRIVACY
Accountable Privacy Management in BC s Public Sector Contents Accountable Privacy Management In BC s Public Sector 2 INTRODUCTION 3 What is accountability? 4 Steps to setting up the program 4 A. PRIVACY
(a) the kind of data and the harm that could result if any of those things should occur;
 Cloud Computing This information leaflet aims to advise organisations on the factors they should take into account in considering engaging cloud computing. It explains the relevance of the Personal Data
Cloud Computing This information leaflet aims to advise organisations on the factors they should take into account in considering engaging cloud computing. It explains the relevance of the Personal Data
Cloud Computing. Introduction
 Cloud Computing Introduction This information leaflet aims to advise organisations which are considering engaging cloud computing on the factors they should consider. It explains the relationship between
Cloud Computing Introduction This information leaflet aims to advise organisations which are considering engaging cloud computing on the factors they should consider. It explains the relationship between
Privacy Management Program Toolkit Health Custodians Personal Health Information Act
 Office of the Information and Privacy Commissioner for Nova Scotia Privacy Management Program Toolkit Health Custodians Personal Health Information Act Introduction: This toolkit was prepared by the Information
Office of the Information and Privacy Commissioner for Nova Scotia Privacy Management Program Toolkit Health Custodians Personal Health Information Act Introduction: This toolkit was prepared by the Information
Guidance on the Use of Portable Storage Devices 1
 Guidance on the Use of Portable Storage Devices Introduction Portable storage devices ( PSDs ) such as USB flash memories or drives, notebook computers or backup tapes provide a convenient means to store
Guidance on the Use of Portable Storage Devices Introduction Portable storage devices ( PSDs ) such as USB flash memories or drives, notebook computers or backup tapes provide a convenient means to store
Guidance for Data Users on the Collection and Use of Personal Data through the Internet 1
 Guidance for Data Users on the Collection and Use of Personal Data through the Internet Introduction Operating online businesses or services, whether by commercial enterprises, non-government organisations
Guidance for Data Users on the Collection and Use of Personal Data through the Internet Introduction Operating online businesses or services, whether by commercial enterprises, non-government organisations
Self-Assessment of a Comprehensive Privacy Programme: A Tool for Practitioners
 Self-Assessment of a Comprehensive Privacy Programme: A Tool for Practitioners The Accountability Project ( the Project ) is pleased to release Self-Assessment of a Comprehensive Privacy Programme: A Tool
Self-Assessment of a Comprehensive Privacy Programme: A Tool for Practitioners The Accountability Project ( the Project ) is pleased to release Self-Assessment of a Comprehensive Privacy Programme: A Tool
Mandatory Provident Fund Schemes Authority COMPLIANCE STANDARDS FOR MPF APPROVED TRUSTEES. First Edition July 2005. Hong Kong
 Mandatory Provident Fund Schemes Authority COMPLIANCE STANDARDS FOR MPF APPROVED TRUSTEES First Edition July 2005 Hong Kong Contents Glossary...2 Introduction to Standards...4 Interpretation Section...6
Mandatory Provident Fund Schemes Authority COMPLIANCE STANDARDS FOR MPF APPROVED TRUSTEES First Edition July 2005 Hong Kong Contents Glossary...2 Introduction to Standards...4 Interpretation Section...6
Information Governance Strategy & Policy
 Information Governance Strategy & Policy March 2014 CONTENT Page 1 Introduction 1 2 Strategic Aims 1 3 Policy 2 4 Responsibilities 3 5 Information Governance Reporting Structure 4 6 Managing Information
Information Governance Strategy & Policy March 2014 CONTENT Page 1 Introduction 1 2 Strategic Aims 1 3 Policy 2 4 Responsibilities 3 5 Information Governance Reporting Structure 4 6 Managing Information
Personal data privacy protection: what mobile apps developers and their clients should know
 Personal data privacy protection: what mobile Introduction This technical information leaflet aims to highlight the privacy implications that mobile applications ( mobile apps ) developers (including organisations
Personal data privacy protection: what mobile Introduction This technical information leaflet aims to highlight the privacy implications that mobile applications ( mobile apps ) developers (including organisations
Corporate Policy and Strategy Committee
 Corporate Policy and Strategy Committee 10am, Tuesday, 30 September 2014 Information Governance Policies Item number Report number Executive/routine Wards All Executive summary Information is a key asset
Corporate Policy and Strategy Committee 10am, Tuesday, 30 September 2014 Information Governance Policies Item number Report number Executive/routine Wards All Executive summary Information is a key asset
Managing General Agents (MGAs) Guideline
 Managing General Agents (MGAs) Guideline JUNE 2013 DRAFT FOR COMMENT BC AUTHORIZED LIFE INSURERS www.fic.gov.bc.ca PURPOSE This draft guideline outlines best practices that the Financial Institutions Commission
Managing General Agents (MGAs) Guideline JUNE 2013 DRAFT FOR COMMENT BC AUTHORIZED LIFE INSURERS www.fic.gov.bc.ca PURPOSE This draft guideline outlines best practices that the Financial Institutions Commission
GUIDANCE NOTE ON OUTSOURCING
 GN 14 GUIDANCE NOTE ON OUTSOURCING Office of the Commissioner of Insurance Contents Page I. Introduction.. 1 II. Application...... 1 III. Interpretation.... 2 IV. Legal and Regulatory Obligations... 3
GN 14 GUIDANCE NOTE ON OUTSOURCING Office of the Commissioner of Insurance Contents Page I. Introduction.. 1 II. Application...... 1 III. Interpretation.... 2 IV. Legal and Regulatory Obligations... 3
Information Governance Policy
 Information Governance Policy Implementation date: 30 September 2014 Control schedule Approved by Corporate Policy and Strategy Committee Approval date 30 September 2014 Senior Responsible Officer Kirsty-Louise
Information Governance Policy Implementation date: 30 September 2014 Control schedule Approved by Corporate Policy and Strategy Committee Approval date 30 September 2014 Senior Responsible Officer Kirsty-Louise
Information Governance Policy
 Information Governance Policy Version: 4 Bodies consulted: Caldicott Guardian, IM&T Directors Approved by: MT Date Approved: 27/10/2015 Lead Manager: Governance Manager Responsible Director: SIRO Date
Information Governance Policy Version: 4 Bodies consulted: Caldicott Guardian, IM&T Directors Approved by: MT Date Approved: 27/10/2015 Lead Manager: Governance Manager Responsible Director: SIRO Date
Information Integrity & Data Management
 Group Standard Information Integrity & Data Management Serco recognises its responsibility to ensure that any information and data produced meets customer, legislative and regulatory requirements and is
Group Standard Information Integrity & Data Management Serco recognises its responsibility to ensure that any information and data produced meets customer, legislative and regulatory requirements and is
CLOUD COMPUTING FOR SMALL- AND MEDIUM-SIZED ENTERPRISES:
 CLOUD COMPUTING FOR SMALL- AND MEDIUM-SIZED ENTERPRISES: Privacy Responsibilities and Considerations Cloud computing is the delivery of computing services over the Internet, and it offers many potential
CLOUD COMPUTING FOR SMALL- AND MEDIUM-SIZED ENTERPRISES: Privacy Responsibilities and Considerations Cloud computing is the delivery of computing services over the Internet, and it offers many potential
Policy Document Control Page
 Policy Document Control Page Title Title: Information Governance Policy Version: 5 Reference Number: CO44 Keywords: Information Governance Supersedes Supersedes: Version 4 Description of Amendment(s):
Policy Document Control Page Title Title: Information Governance Policy Version: 5 Reference Number: CO44 Keywords: Information Governance Supersedes Supersedes: Version 4 Description of Amendment(s):
Align Technology. Data Protection Binding Corporate Rules Processor Policy. 2014 Align Technology, Inc. All rights reserved.
 Align Technology Data Protection Binding Corporate Rules Processor Policy Confidential Contents INTRODUCTION TO THIS POLICY 3 PART I: BACKGROUND AND ACTIONS 4 PART II: PROCESSOR OBLIGATIONS 6 PART III:
Align Technology Data Protection Binding Corporate Rules Processor Policy Confidential Contents INTRODUCTION TO THIS POLICY 3 PART I: BACKGROUND AND ACTIONS 4 PART II: PROCESSOR OBLIGATIONS 6 PART III:
Operations. Group Standard. Business Operations process forms the core of all our business activities
 Standard Operations Business Operations process forms the core of all our business activities SMS-GS-O1 Operations December 2014 v1.1 Serco Public Document Details Document Details erence SMS GS-O1: Operations
Standard Operations Business Operations process forms the core of all our business activities SMS-GS-O1 Operations December 2014 v1.1 Serco Public Document Details Document Details erence SMS GS-O1: Operations
Human Services Quality Framework. User Guide
 Human Services Quality Framework User Guide Purpose The purpose of the user guide is to assist in interpreting and applying the Human Services Quality Standards and associated indicators across all service
Human Services Quality Framework User Guide Purpose The purpose of the user guide is to assist in interpreting and applying the Human Services Quality Standards and associated indicators across all service
GUIDANCE FOR MANAGING THIRD-PARTY RISK
 GUIDANCE FOR MANAGING THIRD-PARTY RISK Introduction An institution s board of directors and senior management are ultimately responsible for managing activities conducted through third-party relationships,
GUIDANCE FOR MANAGING THIRD-PARTY RISK Introduction An institution s board of directors and senior management are ultimately responsible for managing activities conducted through third-party relationships,
Head of Information & Communications Technology Responsible work team: ICT Security. Key point summary... 2
 Policy Procedure Information security policy Policy number: 442 Old instruction number: MAN:F005:a1 Issue date: 24 August 2006 Reviewed as current: 11 July 2014 Owner: Head of Information & Communications
Policy Procedure Information security policy Policy number: 442 Old instruction number: MAN:F005:a1 Issue date: 24 August 2006 Reviewed as current: 11 July 2014 Owner: Head of Information & Communications
Issue 1.0. UoG/ILS/IS 001. Information Security and Assurance Policy. Information Security and Compliance Manager
 Document Reference Number Date Title Author Owning Department Version Approval Date Review Date Approving Body UoG/ILS/IS 001 January 2016 Information Security and Assurance Policy Information Security
Document Reference Number Date Title Author Owning Department Version Approval Date Review Date Approving Body UoG/ILS/IS 001 January 2016 Information Security and Assurance Policy Information Security
Personal Data (Privacy) Ordinance and Electronic Health Record Sharing System (Points to Note for Healthcare Providers and Healthcare Professionals)
 Personal Data (Privacy) Ordinance and Electronic Health Record Sharing System (Points to Note for Healthcare Providers and Healthcare Professionals) The Electronic Health Record Sharing System Ordinance
Personal Data (Privacy) Ordinance and Electronic Health Record Sharing System (Points to Note for Healthcare Providers and Healthcare Professionals) The Electronic Health Record Sharing System Ordinance
White Paper on Financial Institution Vendor Management
 White Paper on Financial Institution Vendor Management Virtually every organization in the modern economy relies to some extent on third-party vendors that facilitate business operations in a wide variety
White Paper on Financial Institution Vendor Management Virtually every organization in the modern economy relies to some extent on third-party vendors that facilitate business operations in a wide variety
Privacy and Security Framework, February 2010
 Privacy and Security Framework, February 2010 Updated April 2014 Our Vision Better data. Better decisions. Healthier Canadians. Our Mandate To lead the development and maintenance of comprehensive and
Privacy and Security Framework, February 2010 Updated April 2014 Our Vision Better data. Better decisions. Healthier Canadians. Our Mandate To lead the development and maintenance of comprehensive and
Cloud Computing and Privacy Toolkit. Protecting Privacy Online. May 2016 CLOUD COMPUTING AND PRIVACY TOOLKIT 1
 Cloud Computing and Privacy Toolkit Protecting Privacy Online May 2016 CLOUD COMPUTING AND PRIVACY TOOLKIT 1 Table of Contents ABOUT THIS TOOLKIT... 4 What is this Toolkit?... 4 Purpose of this Toolkit...
Cloud Computing and Privacy Toolkit Protecting Privacy Online May 2016 CLOUD COMPUTING AND PRIVACY TOOLKIT 1 Table of Contents ABOUT THIS TOOLKIT... 4 What is this Toolkit?... 4 Purpose of this Toolkit...
Guidance on Personal Data Erasure and Anonymisation 1
 Guidance on Personal Data Erasure and Anonymisation Introduction Data users engaged in the collection, holding, processing or use of personal data must carefully consider how to erase such personal data
Guidance on Personal Data Erasure and Anonymisation Introduction Data users engaged in the collection, holding, processing or use of personal data must carefully consider how to erase such personal data
Information Governance Strategy
 Information Governance Strategy Document Status Draft Version: V2.1 DOCUMENT CHANGE HISTORY Initiated by Date Author Information Governance Requirements September 2007 Information Governance Group Version
Information Governance Strategy Document Status Draft Version: V2.1 DOCUMENT CHANGE HISTORY Initiated by Date Author Information Governance Requirements September 2007 Information Governance Group Version
Exercising Your Right of Consent to and Opt-out from Direct Marketing Activities under the Personal Data (Privacy) Ordinance 1
 Exercising Your Right of Consent to and Opt-out from Direct Marketing Activities under the Personal Data (Privacy) Ordinance 1 It is common for members of the public to receive unsolicited telephone calls,
Exercising Your Right of Consent to and Opt-out from Direct Marketing Activities under the Personal Data (Privacy) Ordinance 1 It is common for members of the public to receive unsolicited telephone calls,
Information Governance Policy
 Information Governance Policy Information Governance Policy Issue Date: June 2014 Document Number: POL_1008 Prepared by: Information Governance Senior Manager Insert heading depending on Insert line heading
Information Governance Policy Information Governance Policy Issue Date: June 2014 Document Number: POL_1008 Prepared by: Information Governance Senior Manager Insert heading depending on Insert line heading
AIRBUS GROUP BINDING CORPORATE RULES
 1 AIRBUS GROUP BINDING CORPORATE RULES 2 Introduction The Binding Corporate Rules (hereinafter BCRs ) of the Airbus Group finalize the Airbus Group s provisions on the protection of Personal Data. These
1 AIRBUS GROUP BINDING CORPORATE RULES 2 Introduction The Binding Corporate Rules (hereinafter BCRs ) of the Airbus Group finalize the Airbus Group s provisions on the protection of Personal Data. These
LEEDS BECKETT UNIVERSITY. Information Security Policy. 1.0 Introduction
 LEEDS BECKETT UNIVERSITY Information Security Policy 1.0 Introduction 1.1 Information in all of its forms is crucial to the effective functioning and good governance of our University. We are committed
LEEDS BECKETT UNIVERSITY Information Security Policy 1.0 Introduction 1.1 Information in all of its forms is crucial to the effective functioning and good governance of our University. We are committed
What to do When Faced With a Privacy Breach: Guidelines for the Health Sector ANN CAVOUKIAN, PH.D. COMMISSIONER
 What to do When Faced With a Privacy Breach: Guidelines for the Health Sector ANN CAVOUKIAN, PH.D. COMMISSIONER INFORMATION AND PRIVACY COMMISSIONER/ONTARIO Table of Contents What is a privacy breach?...1
What to do When Faced With a Privacy Breach: Guidelines for the Health Sector ANN CAVOUKIAN, PH.D. COMMISSIONER INFORMATION AND PRIVACY COMMISSIONER/ONTARIO Table of Contents What is a privacy breach?...1
How To Ensure Health Information Is Protected
 pic pic CIHI Submission: 2011 Prescribed Entity Review October 2011 Who We Are Established in 1994, CIHI is an independent, not-for-profit corporation that provides essential information on Canada s health
pic pic CIHI Submission: 2011 Prescribed Entity Review October 2011 Who We Are Established in 1994, CIHI is an independent, not-for-profit corporation that provides essential information on Canada s health
INFORMATION GOVERNANCE POLICY & FRAMEWORK
 INFORMATION GOVERNANCE POLICY & FRAMEWORK Version 1.2 Committee Approved by Audit Committee Date Approved 5 March 2015 Author: Responsible Lead: Associate IG Specialist, YHCS Corporate & Governance Manger
INFORMATION GOVERNANCE POLICY & FRAMEWORK Version 1.2 Committee Approved by Audit Committee Date Approved 5 March 2015 Author: Responsible Lead: Associate IG Specialist, YHCS Corporate & Governance Manger
Information Governance Strategy :
 Item 11 Strategy Strategy : Date Issued: Date To Be Reviewed: VOY xx Annually 1 Policy Title: Strategy Supersedes: All previous Strategies 18/12/13: Initial draft Description of Amendments 19/12/13: Update
Item 11 Strategy Strategy : Date Issued: Date To Be Reviewed: VOY xx Annually 1 Policy Title: Strategy Supersedes: All previous Strategies 18/12/13: Initial draft Description of Amendments 19/12/13: Update
Auditing data protection a guide to ICO data protection audits
 Auditing data protection a guide to ICO data protection audits Contents Executive summary 3 1. Audit programme development 5 Audit planning and risk assessment 2. Audit approach 6 Gathering evidence Audit
Auditing data protection a guide to ICO data protection audits Contents Executive summary 3 1. Audit programme development 5 Audit planning and risk assessment 2. Audit approach 6 Gathering evidence Audit
DATA PROTECTION POLICY
 Reference number Approved by Information Management and Technology Board Date approved 14 th May 2012 Version 1.1 Last revised N/A Review date May 2015 Category Information Assurance Owner Data Protection
Reference number Approved by Information Management and Technology Board Date approved 14 th May 2012 Version 1.1 Last revised N/A Review date May 2015 Category Information Assurance Owner Data Protection
Align Technology. Data Protection Binding Corporate Rules Controller Policy. 2014 Align Technology, Inc. All rights reserved.
 Align Technology Data Protection Binding Corporate Rules Controller Policy Contents INTRODUCTION 3 PART I: BACKGROUND AND ACTIONS 4 PART II: CONTROLLER OBLIGATIONS 6 PART III: APPENDICES 13 2 P a g e INTRODUCTION
Align Technology Data Protection Binding Corporate Rules Controller Policy Contents INTRODUCTION 3 PART I: BACKGROUND AND ACTIONS 4 PART II: CONTROLLER OBLIGATIONS 6 PART III: APPENDICES 13 2 P a g e INTRODUCTION
Cloud Computing Contracts. October 11, 2012
 Cloud Computing Contracts October 11, 2012 Lorene Novakowski Karam Bayrakal Covering Cloud Computing Cloud Computing Defined Models Manage Cloud Computing Risk Mitigation Strategy Privacy Contracts Best
Cloud Computing Contracts October 11, 2012 Lorene Novakowski Karam Bayrakal Covering Cloud Computing Cloud Computing Defined Models Manage Cloud Computing Risk Mitigation Strategy Privacy Contracts Best
Processor Binding Corporate Rules (BCRs), for intra-group transfers of personal data to non EEA countries
 Processor Binding Corporate Rules (BCRs), for intra-group transfers of personal data to non EEA countries Sopra HR Software as a Data Processor Sopra HR Software, 2014 / Ref. : 20141120-101114-m 1/32 1.
Processor Binding Corporate Rules (BCRs), for intra-group transfers of personal data to non EEA countries Sopra HR Software as a Data Processor Sopra HR Software, 2014 / Ref. : 20141120-101114-m 1/32 1.
Audit and Performance Committee Report
 Audit and Performance Committee Report Date: 3 February 2016 Classification: Title: Wards Affected: Financial Summary: Report of: Author: General Release Maintaining High Ethical Standards at the City
Audit and Performance Committee Report Date: 3 February 2016 Classification: Title: Wards Affected: Financial Summary: Report of: Author: General Release Maintaining High Ethical Standards at the City
Corporate Information Security Policy
 Corporate Information Security Policy. A guide to the Council s approach to safeguarding information resources. September 2015 Contents Page 1. Introduction 1 2. Information Security Framework 2 3. Objectives
Corporate Information Security Policy. A guide to the Council s approach to safeguarding information resources. September 2015 Contents Page 1. Introduction 1 2. Information Security Framework 2 3. Objectives
Supervisory Policy Manual
 This module should be read in conjunction with the Introduction and with the Glossary, which contains an explanation of abbreviations and other terms used in this Manual. If reading on-line, click on blue
This module should be read in conjunction with the Introduction and with the Glossary, which contains an explanation of abbreviations and other terms used in this Manual. If reading on-line, click on blue
Information Governance and Management Standards for the Health Identifiers Operator in Ireland
 Information Governance and Management Standards for the Health Identifiers Operator in Ireland 30 July 2015 About the The (the Authority or HIQA) is the independent Authority established to drive high
Information Governance and Management Standards for the Health Identifiers Operator in Ireland 30 July 2015 About the The (the Authority or HIQA) is the independent Authority established to drive high
Passenger Protect Program Transport Canada
 AUDIT REPORT OF THE PRIVACY COMMISSIONER OF CANADA Passenger Protect Program Transport Canada Section 37 of the Privacy Act 2009 AUDIT OF PASSENGER PROTECT PROGRAM, TRANSPORT CANADA The audit work reported
AUDIT REPORT OF THE PRIVACY COMMISSIONER OF CANADA Passenger Protect Program Transport Canada Section 37 of the Privacy Act 2009 AUDIT OF PASSENGER PROTECT PROGRAM, TRANSPORT CANADA The audit work reported
Information Governance Policy
 Information Governance Policy Version 1.1 Responsible Person Information Governance Manager Lead Director Head of Corporate Services Consultation Route Information Governance Steering Group Approval Route
Information Governance Policy Version 1.1 Responsible Person Information Governance Manager Lead Director Head of Corporate Services Consultation Route Information Governance Steering Group Approval Route
Report of the Information & Privacy Commissioner/Ontario. Review of the Canadian Institute for Health Information:
 Information and Privacy Commissioner of Ontario Report of the Information & Privacy Commissioner/Ontario Review of the Canadian Institute for Health Information: A Prescribed Entity under the Personal
Information and Privacy Commissioner of Ontario Report of the Information & Privacy Commissioner/Ontario Review of the Canadian Institute for Health Information: A Prescribed Entity under the Personal
Preparation of a Rail Safety Management System Guideline
 Preparation of a Rail Safety Management System Guideline Page 1 of 99 Version History Version No. Approved by Date approved Review date 1 By 20 January 2014 Guideline for Preparation of a Safety Management
Preparation of a Rail Safety Management System Guideline Page 1 of 99 Version History Version No. Approved by Date approved Review date 1 By 20 January 2014 Guideline for Preparation of a Safety Management
1.1 An initial request to enter into a contractual arrangement may be initiated by either Massey University or another party (Other Party).
 CONTRACT MANAGEMENT PROCEDURE Section Risk Management Contact Risk Manager Last Review February 2013 Next Review February 2016 Approval Not required Procedures Contract Initiation Request Mandatory Guidance
CONTRACT MANAGEMENT PROCEDURE Section Risk Management Contact Risk Manager Last Review February 2013 Next Review February 2016 Approval Not required Procedures Contract Initiation Request Mandatory Guidance
FIRST DATA CORPORATION PROCESSOR DATA PROTECTION STANDARDS
 FIRST DATA CORPORATION PROCESSOR DATA PROTECTION STANDARDS As a world leader in electronic commerce and payment services, First Data Corporation and its subsidiaries ( First Data entity or entities ),
FIRST DATA CORPORATION PROCESSOR DATA PROTECTION STANDARDS As a world leader in electronic commerce and payment services, First Data Corporation and its subsidiaries ( First Data entity or entities ),
RISK AND COMPLIANCE COMMITTEE CHARTER
 1. GENERAL SCOPE AND AUTHORITY 1.1 Introduction This charter governs the operations of the Risk & Compliance Committee of Redflex Holdings Limited (RHL or Company). 1.2 Purpose The Risk & Compliance Committee
1. GENERAL SCOPE AND AUTHORITY 1.1 Introduction This charter governs the operations of the Risk & Compliance Committee of Redflex Holdings Limited (RHL or Company). 1.2 Purpose The Risk & Compliance Committee
Security Incident Management Policy
 Security Incident Management Policy January 2015 Document Version 2.4 Document Status Owner Name Owner Job Title Published Martyn Ward Head of ICT Business Delivery Document ref. Approval Date 27/01/2015
Security Incident Management Policy January 2015 Document Version 2.4 Document Status Owner Name Owner Job Title Published Martyn Ward Head of ICT Business Delivery Document ref. Approval Date 27/01/2015
West Dunbartonshire Council. Follow-up data protection audit report
 West Dunbartonshire Council Follow-up data protection audit report Auditors: Lee Taylor (Audit Team Manager) Jonathan Kay (Engagement Lead Auditor) Data controller contacts: Michael Butler (Data Protection/Information
West Dunbartonshire Council Follow-up data protection audit report Auditors: Lee Taylor (Audit Team Manager) Jonathan Kay (Engagement Lead Auditor) Data controller contacts: Michael Butler (Data Protection/Information
Financial Management Framework >> Overview Diagram
 June 2012 The State of Queensland (Queensland Treasury) June 2012 Except where otherwise noted you are free to copy, communicate and adapt this work, as long as you attribute the authors. This document
June 2012 The State of Queensland (Queensland Treasury) June 2012 Except where otherwise noted you are free to copy, communicate and adapt this work, as long as you attribute the authors. This document
The potential legal consequences of a personal data breach
 The potential legal consequences of a personal data breach Tue Goldschmieding, Partner 16 April 2015 The potential legal consequences of a personal data breach 15 April 2015 Contents 1. Definitions 2.
The potential legal consequences of a personal data breach Tue Goldschmieding, Partner 16 April 2015 The potential legal consequences of a personal data breach 15 April 2015 Contents 1. Definitions 2.
PRINCIPLES ON OUTSOURCING OF FINANCIAL SERVICES FOR MARKET INTERMEDIARIES
 PRINCIPLES ON OUTSOURCING OF FINANCIAL SERVICES FOR MARKET INTERMEDIARIES TECHNICAL COMMITTEE OF THE INTERNATIONAL ORGANIZATION OF SECURITIES COMMISSIONS FEBRUARY 2005 Preamble The IOSCO Technical Committee
PRINCIPLES ON OUTSOURCING OF FINANCIAL SERVICES FOR MARKET INTERMEDIARIES TECHNICAL COMMITTEE OF THE INTERNATIONAL ORGANIZATION OF SECURITIES COMMISSIONS FEBRUARY 2005 Preamble The IOSCO Technical Committee
Who s next after TalkTalk?
 Who s next after TalkTalk? Frequently Asked Questions on Cyber Risk Fraud threat to millions of TalkTalk customers TalkTalk cyber-attack: website hit by significant breach These are just two of the many
Who s next after TalkTalk? Frequently Asked Questions on Cyber Risk Fraud threat to millions of TalkTalk customers TalkTalk cyber-attack: website hit by significant breach These are just two of the many
IT OUTSOURCING SECURITY
 IT OUTSOURCING SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
IT OUTSOURCING SECURITY February 2008 The Government of the Hong Kong Special Administrative Region The contents of this document remain the property of, and may not be reproduced in whole or in part without
CITY UNIVERSITY OF HONG KONG
 CITY UNIVERSITY OF HONG KONG (Approved by the Information Strategy and Governance Committee in December 2013) PUBLIC Date of Issue: 2013-12-24 Document Control Document Owner Classification Publication
CITY UNIVERSITY OF HONG KONG (Approved by the Information Strategy and Governance Committee in December 2013) PUBLIC Date of Issue: 2013-12-24 Document Control Document Owner Classification Publication
Information Governance Strategy. Version No 2.0
 Plymouth Community Healthcare CIC Information Governance Strategy Version No 2.0 Notice to staff using a paper copy of this guidance. The policies and procedures page of PCH Intranet holds the most recent
Plymouth Community Healthcare CIC Information Governance Strategy Version No 2.0 Notice to staff using a paper copy of this guidance. The policies and procedures page of PCH Intranet holds the most recent
Caedmon College Whitby
 Caedmon College Whitby Data Protection and Information Security Policy College Governance Status This policy was re-issued in June 2014 and was adopted by the Governing Body on 26 June 2014. It will be
Caedmon College Whitby Data Protection and Information Security Policy College Governance Status This policy was re-issued in June 2014 and was adopted by the Governing Body on 26 June 2014. It will be
Financial Services Guidance Note Outsourcing
 Financial Services Guidance Note Issued: April 2005 Revised: August 2007 Table of Contents 1. Introduction... 3 1.1 Background... 3 1.2 Definitions... 3 2. Guiding Principles... 5 3. Key Risks of... 14
Financial Services Guidance Note Issued: April 2005 Revised: August 2007 Table of Contents 1. Introduction... 3 1.1 Background... 3 1.2 Definitions... 3 2. Guiding Principles... 5 3. Key Risks of... 14
ASTRAZENECA GLOBAL POLICY SAFEGUARDING COMPANY ASSETS AND RESOURCES
 ASTRAZENECA GLOBAL POLICY SAFEGUARDING COMPANY ASSETS AND RESOURCES THIS POLICY SETS OUT THE REQUIREMENTS FOR SAFEGUARDING COMPANY ASSETS AND RESOURCES TO PROTECT PATIENTS, STAFF, PRODUCTS, PROPERTY AND
ASTRAZENECA GLOBAL POLICY SAFEGUARDING COMPANY ASSETS AND RESOURCES THIS POLICY SETS OUT THE REQUIREMENTS FOR SAFEGUARDING COMPANY ASSETS AND RESOURCES TO PROTECT PATIENTS, STAFF, PRODUCTS, PROPERTY AND
GUIDELINE ON THE APPLICATION OF THE OUTSOURCING REQUIREMENTS UNDER THE FSA RULES IMPLEMENTING MIFID AND THE CRD IN THE UK
 GUIDELINE ON THE APPLICATION OF THE OUTSOURCING REQUIREMENTS UNDER THE FSA RULES IMPLEMENTING MIFID AND THE CRD IN THE UK This Guideline does not purport to be a definitive guide, but is instead a non-exhaustive
GUIDELINE ON THE APPLICATION OF THE OUTSOURCING REQUIREMENTS UNDER THE FSA RULES IMPLEMENTING MIFID AND THE CRD IN THE UK This Guideline does not purport to be a definitive guide, but is instead a non-exhaustive
PRINCIPLES OF CORPORATE GOVERNANCE FOR SUPERVISED INSTITUTIONS
 PRINCIPLES OF CORPORATE GOVERNANCE FOR SUPERVISED INSTITUTIONS Content of principles I. ORGANISATION AND ORGANISATIONAL STRUCTURE 1. 1 The organisation of a supervised institution should enable meeting
PRINCIPLES OF CORPORATE GOVERNANCE FOR SUPERVISED INSTITUTIONS Content of principles I. ORGANISATION AND ORGANISATIONAL STRUCTURE 1. 1 The organisation of a supervised institution should enable meeting
Information Governance Strategy
 Information Governance Strategy To whom this document applies: All Trust staff, including agency and contractors Procedural Documents Approval Committee Issue Date: January 2010 Version 1 Document reference:
Information Governance Strategy To whom this document applies: All Trust staff, including agency and contractors Procedural Documents Approval Committee Issue Date: January 2010 Version 1 Document reference:
Information Governance Strategy and Policy. OFFICIAL Ownership: Information Governance Group Date Issued: 15/01/2015 Version: 2.
 Information Governance Strategy and Policy Ownership: Information Governance Group Date Issued: 15/01/2015 Version: 2.0 Status: Final Revision and Signoff Sheet Change Record Date Author Version Comments
Information Governance Strategy and Policy Ownership: Information Governance Group Date Issued: 15/01/2015 Version: 2.0 Status: Final Revision and Signoff Sheet Change Record Date Author Version Comments
Data Protection Breach Reporting Procedure
 Central Bedfordshire Council www.centralbedfordshire.gov.uk Data Protection Breach Reporting Procedure October 2015 Security Classification: Not Protected 1 Approval History Version No Approved by Approval
Central Bedfordshire Council www.centralbedfordshire.gov.uk Data Protection Breach Reporting Procedure October 2015 Security Classification: Not Protected 1 Approval History Version No Approved by Approval
Operational Risk Publication Date: May 2015. 1. Operational Risk... 3
 OPERATIONAL RISK Contents 1. Operational Risk... 3 1.1 Legislation... 3 1.2 Guidance... 3 1.3 Risk management process... 4 1.4 Risk register... 7 1.5 EBA Guidelines on the Security of Internet Payments...
OPERATIONAL RISK Contents 1. Operational Risk... 3 1.1 Legislation... 3 1.2 Guidance... 3 1.3 Risk management process... 4 1.4 Risk register... 7 1.5 EBA Guidelines on the Security of Internet Payments...
Office of the Regulator of Community Interest Companies: information and guidance notes. Chapter 9: Corporate Governance MARCH 2013
 Office of the Regulator of Community Interest Companies: information and guidance notes Chapter 9: Corporate Governance MARCH 2013 Contents 9.1. Role of Directors and Members...3 9.1.1. Corporate Governance
Office of the Regulator of Community Interest Companies: information and guidance notes Chapter 9: Corporate Governance MARCH 2013 Contents 9.1. Role of Directors and Members...3 9.1.1. Corporate Governance
Proposed guidance for firms outsourcing to the cloud and other third-party IT services
 Guidance consultation 15/6 Proposed guidance for firms outsourcing to the cloud and other third-party IT services November 2015 1. Introduction and consultation 1.1 The purpose of this draft guidance is
Guidance consultation 15/6 Proposed guidance for firms outsourcing to the cloud and other third-party IT services November 2015 1. Introduction and consultation 1.1 The purpose of this draft guidance is
Criminal Injuries Compensation Authority. Data protection audit report
 Criminal Injuries Compensation Authority Data protection audit report Executive summary January 2016 1. Background The Information Commissioner is responsible for enforcing and promoting compliance with
Criminal Injuries Compensation Authority Data protection audit report Executive summary January 2016 1. Background The Information Commissioner is responsible for enforcing and promoting compliance with
ING Group Compliance Risk Management Charter and Framework
 ING Group Compliance Risk Management Charter and Framework Corporate Compliance Risk Management ING GROUP COMPLIANCE RISK MANAGEMENT CHARTER AND FRAMEWORK Information sheet Target audience: All employees
ING Group Compliance Risk Management Charter and Framework Corporate Compliance Risk Management ING GROUP COMPLIANCE RISK MANAGEMENT CHARTER AND FRAMEWORK Information sheet Target audience: All employees
Compliance. Group Standard
 Group Standard Compliance Serco is committed to good governance practices and the management of risks supported by a robust business compliance process SMS-GS-G2 Compliance July 2014 v1.0 Serco Public
Group Standard Compliance Serco is committed to good governance practices and the management of risks supported by a robust business compliance process SMS-GS-G2 Compliance July 2014 v1.0 Serco Public
The CIPM certification is comprised of two domains: Privacy Program Governance (I) and Privacy Program Operational Life Cycle (II).
 Page 1 of 7 The CIPM certification is comprised of two domains: Privacy Program Governance (I) and Privacy Program Operational Life Cycle (II). Domain I provides a solid foundation for the governance of
Page 1 of 7 The CIPM certification is comprised of two domains: Privacy Program Governance (I) and Privacy Program Operational Life Cycle (II). Domain I provides a solid foundation for the governance of
Appendix 14 CORPORATE GOVERNANCE CODE AND CORPORATE GOVERNANCE REPORT
 Appendix 14 CORPORATE GOVERNANCE CODE AND CORPORATE GOVERNANCE REPORT The Code This Code sets out the principles of good corporate governance, and two levels of recommendations: code provisions; and recommended
Appendix 14 CORPORATE GOVERNANCE CODE AND CORPORATE GOVERNANCE REPORT The Code This Code sets out the principles of good corporate governance, and two levels of recommendations: code provisions; and recommended
Information Governance Policy
 Information Governance Policy Reference: Information Governance Policy Date Approved: April 2013 Approving Body: Board of Trustees Implementation Date: April 2013 Version: 6 Supersedes: 5 Stakeholder groups
Information Governance Policy Reference: Information Governance Policy Date Approved: April 2013 Approving Body: Board of Trustees Implementation Date: April 2013 Version: 6 Supersedes: 5 Stakeholder groups
OFFICIAL. NCC Records Management and Disposal Policy
 NCC Records Management and Disposal Policy Issue No: V1.0 Reference: NCC/IG4 Date of Origin: 12/11/2013 Date of this Issue: 14/01/2014 1 P a g e DOCUMENT TITLE NCC Records Management and Disposal Policy
NCC Records Management and Disposal Policy Issue No: V1.0 Reference: NCC/IG4 Date of Origin: 12/11/2013 Date of this Issue: 14/01/2014 1 P a g e DOCUMENT TITLE NCC Records Management and Disposal Policy
Information Governance Policy (incorporating IM&T Security)
 (incorporating IM&T Security) ONCE PRINTED OFF, THIS IS AN UNCONTROLLED DOCUMENT. PLEASE CHECK THE INTRANET FOR THE MOST UP TO DATE COPY Target Audience: All staff employed or working on behalf of the
(incorporating IM&T Security) ONCE PRINTED OFF, THIS IS AN UNCONTROLLED DOCUMENT. PLEASE CHECK THE INTRANET FOR THE MOST UP TO DATE COPY Target Audience: All staff employed or working on behalf of the
ROYAL AUSTRALASIAN COLLEGE OF SURGEONS
 1. SCOPE This policy details the College s privacy policy and related information handling practices and gives guidelines for access to any personal information retained by the College. This includes personal
1. SCOPE This policy details the College s privacy policy and related information handling practices and gives guidelines for access to any personal information retained by the College. This includes personal
Published by the National Regulatory System for Community Housing Directorate. Document Identification: 003-04-13/NRSD. Publication date: January 2014
 Evidence guidelines Published by the National Regulatory System for Community Housing Directorate. Document Identification: 003-04-13/NRSD Publication date: January 2014 Supported by the Commonwealth Government
Evidence guidelines Published by the National Regulatory System for Community Housing Directorate. Document Identification: 003-04-13/NRSD Publication date: January 2014 Supported by the Commonwealth Government
INFORMATION GOVERNANCE AND SECURITY 1 POLICY DRAFTED BY: INFORMATION GOVERNANCE LEAD 2 ACCOUNTABLE DIRECTOR: SENIOR INFORMATION RISK OWNER
 INFORMATION GOVERNANCE AND SECURITY 1 POLICY DRAFTED BY: INFORMATION GOVERNANCE LEAD 2 ACCOUNTABLE DIRECTOR: SENIOR INFORMATION RISK OWNER 3 APPLIES TO: ALL STAFF 4 COMMITTEE & DATE APPROVED: AUDIT COMMITTEE
INFORMATION GOVERNANCE AND SECURITY 1 POLICY DRAFTED BY: INFORMATION GOVERNANCE LEAD 2 ACCOUNTABLE DIRECTOR: SENIOR INFORMATION RISK OWNER 3 APPLIES TO: ALL STAFF 4 COMMITTEE & DATE APPROVED: AUDIT COMMITTEE
Request for feedback on the revised Code of Governance for NHS Foundation Trusts
 Request for feedback on the revised Code of Governance for NHS Foundation Trusts Introduction 8 November 2013 One of Monitor s key objectives is to make sure that public providers are well led. To this
Request for feedback on the revised Code of Governance for NHS Foundation Trusts Introduction 8 November 2013 One of Monitor s key objectives is to make sure that public providers are well led. To this
How To Understand The Importance Of Internal Control
 FINANCIAL REPORTING COUNCIL INTERNAL CONTROL REVISED GUIDANCE FOR DIRECTORS ON THE COMBINED CODE OCTOBER 2005 FINANCIAL REPORTING COUNCIL INTERNAL CONTROL REVISED GUIDANCE FOR DIRECTORS ON THE COMBINED
FINANCIAL REPORTING COUNCIL INTERNAL CONTROL REVISED GUIDANCE FOR DIRECTORS ON THE COMBINED CODE OCTOBER 2005 FINANCIAL REPORTING COUNCIL INTERNAL CONTROL REVISED GUIDANCE FOR DIRECTORS ON THE COMBINED
Guide to the National Safety and Quality Health Service Standards for health service organisation boards
 Guide to the National Safety and Quality Health Service Standards for health service organisation boards April 2015 ISBN Print: 978-1-925224-10-8 Electronic: 978-1-925224-11-5 Suggested citation: Australian
Guide to the National Safety and Quality Health Service Standards for health service organisation boards April 2015 ISBN Print: 978-1-925224-10-8 Electronic: 978-1-925224-11-5 Suggested citation: Australian
DATA PROTECTION CORPORATE POLICY
 DATA PROTECTION CORPORATE POLICY Information Management V1.1 03 July 2012 Not protectively marked This policy must be complied with fully by all Members, Officers Agents and Contractors of Plymouth City
DATA PROTECTION CORPORATE POLICY Information Management V1.1 03 July 2012 Not protectively marked This policy must be complied with fully by all Members, Officers Agents and Contractors of Plymouth City
A Guide to Corporate Governance for QFC Authorised Firms
 A Guide to Corporate Governance for QFC Authorised Firms January 2012 Disclaimer The goal of the Qatar Financial Centre Regulatory Authority ( Regulatory Authority ) in producing this document is to provide
A Guide to Corporate Governance for QFC Authorised Firms January 2012 Disclaimer The goal of the Qatar Financial Centre Regulatory Authority ( Regulatory Authority ) in producing this document is to provide
MALAYSIAN TECHNOLOGY DEVELOPMENT CORPORATION SDN. BHD.
 MALAYSIAN TECHNOLOGY DEVELOPMENT CORPORATION SDN. BHD. WHISTLEBLOWING POLICY AND GUIDELINES 16 March 2012 Version 1.0 TABLE OF CONTENTS WHISTLEBLOWING POLICY Page WHISTLEBLOWING GUIDELINES B1 DEFINITION
MALAYSIAN TECHNOLOGY DEVELOPMENT CORPORATION SDN. BHD. WHISTLEBLOWING POLICY AND GUIDELINES 16 March 2012 Version 1.0 TABLE OF CONTENTS WHISTLEBLOWING POLICY Page WHISTLEBLOWING GUIDELINES B1 DEFINITION
Best Practices in Data Management - A Guide for Marketers -
 Best Practices in Data Management - A Guide for Marketers - Prepared with support from the Office of the Privacy Commissioner of Canada s Contributions Program INTRODUCTION As consumers personal information
Best Practices in Data Management - A Guide for Marketers - Prepared with support from the Office of the Privacy Commissioner of Canada s Contributions Program INTRODUCTION As consumers personal information
ISO 27001: Information Security and the Road to Certification
 ISO 27001: Information Security and the Road to Certification White paper Abstract An information security management system (ISMS) is an essential part of an organization s defense against cyberattacks
ISO 27001: Information Security and the Road to Certification White paper Abstract An information security management system (ISMS) is an essential part of an organization s defense against cyberattacks
